softasap.sa-kong
sa-kong
Kong is a flexible and scalable open-source API layer, often referred to as an API Gateway. It works in front of any RESTful API and can be customized with plugins to add extra features beyond its core functions.
Kong was originally developed by Mashape to manage and secure over 15,000 APIs and microservices for its API Marketplace, which processes billions of requests each month for more than 200,000 developers. Today, Kong is utilized by organizations of all sizes in critical applications.
- Scalable: Kong can easily grow to handle more users by adding more machines, keeping response times low.
- Modular: You can add new features (plugins) to Kong that can be configured via a RESTful Admin API.
- Versatile: Kong can be deployed in the cloud or on local servers, whether using one data center or multiple, and it can work with public, private, or invitation-only APIs.
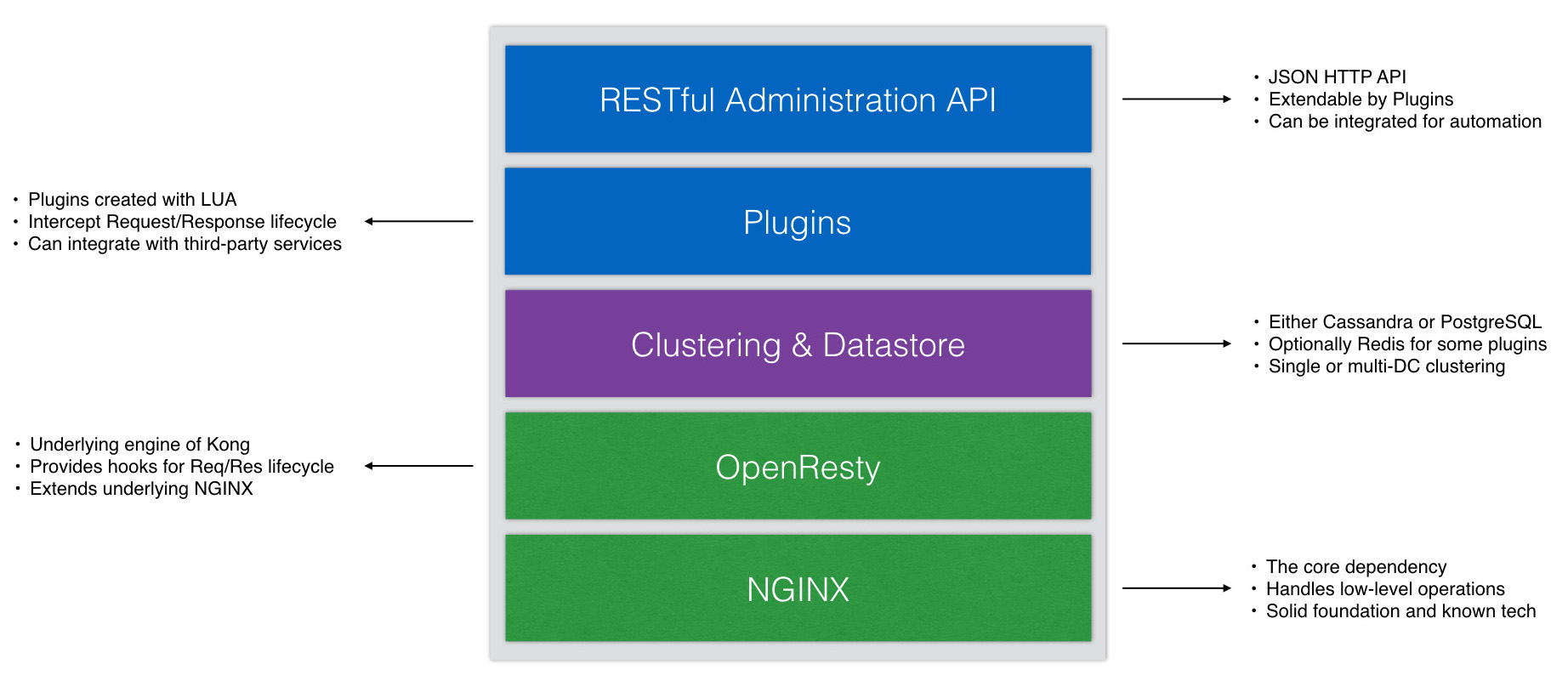
Kong is built on top of Nginx, which makes it stable and efficient. It runs as a Lua application within Nginx, using the lua-nginx-module. Instead of directly using Nginx, Kong is distributed with OpenResty, which comes with lua-nginx-module included. OpenResty is not just a variant of Nginx but a complete package that enhances its functionality.
This design allows for a flexible architecture where Lua scripts (called "plugins") can be activated and used during runtime. Kong's main features include managing databases, routing, and handling plugins, which can be independently developed and easily connected to requests.
Note: The community version of Kong does not have a user interface. You might want to look into open source web UIs like Kong Dashboard or Konga.
In my experience, Kong Dashboard has a more robust development process, though Konga may offer more creative options.
# Install Kong Dashboard
npm install -g kong-dashboard
# Start Kong Dashboard
kong-dashboard start --kong-url http://kong:8001
# Start Kong Dashboard on a custom port
kong-dashboard start \
--kong-url http://kong:8001 \
--port [port]
roles:
- {
role: "sa-kong"
}
Advanced Configuration:
roles:
- {
role: "sa-kong",
kong_version: 2.0.1,
kong_activated_plugins: "bundled,oidc",
kong_luarocks_plugins:
- kong-oidc
kong_admin_http: "0.0.0.0:8001",
kong_admin_https: "127.0.0.1:8444",
kong_proxy_http: "0.0.0.0:8000",
kong_proxy_https: "0.0.0.0:8443",
kong_pg_host: "127.0.0.1",
kong_pg_port: 5432,
kong_pg_user: kong,
kong_pg_password: kong,
kong_pg_database: kong
}
Notes for Future Reference
Third-Party Plugins
kong-oidc
This plugin adds OpenID Connect (OIDC) authentication for users. It connects to an OIDC provider, verifies users, and can manage session states either in browser cookies or server-side storage (like Redis).
After you have the client ID, secret, and OIDC discovery URL, enable the plugin using the following command:
curl -XPOST -d 'name=oidc' -d 'config.client_id=<client_id>' -d 'config.client_secret=<client_secret>' -d 'config.discovery=<OIDC_Discovery_url>' http://kong:8001/plugins
Once enabled, users will be redirected to the Authorization Server for login when accessing any APIs in Kong that use this plugin.
Kong will handle session tokens and will redirect users as necessary.
Setup in Docker
If you want to use the kong-oidc plugin in Docker, start from this Dockerfile:
FROM kong:1.4.0-alpine
LABEL description="Alpine + Kong 1.4.0 + kong-oidc plugin"
RUN apk update && apk add git unzip luarocks
RUN luarocks install kong-oidc
In the image, you can activate plugins using the environment variable KONG_PLUGINS:
KONG_PLUGINS=oidc
Usage with Kubernetes
Here's an example Kubernetes deployment using the plugin:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-kong
annotations:
plugins.konghq.com: oidc
spec:
rules:
- http:
paths:
- path: /graphql
backend:
serviceName: corphub-graphql-service
servicePort: 8082
---
apiVersion: configuration.konghq.com/v1
kind: KongPlugin
metadata:
name: kong-oidc
labels:
global: "true"
config:
client_id: kong
client_secret: XXX
discovery: http://keycloak:8180/auth/realms/master/.well-known/openid-configuration
plugin: oidc
Additional Plugins
- kong-middleman: Creates an extra HTTP POST before sending the original request. GitHub Link
- kong-external-oauth: Lets you use an external OAuth 2.0 provider for API protection. GitHub Link
Postgres Backend Configuration
Your pg_hba.conf file may need to look like this:
local all postgres peer
local all all md5
host all all 127.0.0.1/32 password
host all all 127.0.0.1/32 md5
host all all ::1/128 md5
Reference Links
Dashboards:
- Konga (Kong > 1)
- Kong-Dashboard (Kong > 0.9)
Declarative Config Tools:
Ansible Galaxy Usage
If you installed the sa-kong role with:
ansible-galaxy install softasap.sa-kong
You can reference it in your playbook as follows:
- {
role: "softasap.sa-kong"
}
Copyright and License
The code is dual-licensed under the BSD 3-Clause License and the MIT License. Choose whichever suits your needs.
For updates and discussions, feel free to connect:
- Subscribe for updates at Facebook
- Join discussions on Gitter
- Explore other roles at SoftAsap Roles Registry
- Visit our blog at SoftAsap Blog
